Hashcat for Beginners : Part-1
“hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and OSX, and has facilities to help enable distributed password cracking” :- Kali.org
In simple words i can say we can use Hashcat to crack any password. Hashcat support many hashing algorithms. It provides different attacks that we can use to crack passwords.
As we know we can not reverse HASH so first and normal approach is to guess the password and compare HASH value.
Note : if you are not using Kali linux then you need to download it from it’s official website. LINK
Let’s See how to use Hashcat. Let’s open terminal and type “hashcat” and press enter.
hashcat --help
As we can see hashcat help gives us all the information and also gives us example.
Handles(eg. -d) that we should know before going to see examples.
-a number : attack mode
-m number : type of hash
-o filename : output
Let’s see syntax
hashcat -a number -m number -o OUTPUT.txt HASH.txt WORDLIST.txt
here,
-a defines attack mode
-m defines hash type
-o we want to save output result in OUTPUT.txt file
HASH.txt is file that contain hash values that we want to crack
WORDLIST.txt is file from which we think password can be matched
Now let’s try one example.
Let’s first create md5 hash value for “password” string. In kali Linux we can use md5sum to generate md5 hash value.
Let’s save all this hash value in one file. we will store hash values of following strings “password,internet,Password!,admin,qwerty”
we used tr -d to remove any space and hyphen(-) from md5sum output.
we will use following command
hashcat -m 0 -a 0 hash.txt /usr/share/wordlist/rockyou.txt --force
- -m 0 defines hash type (md5)
- -a 0 defines Dictionary attack
- hash.txt is file in which we have saved all hashes
- we used /usr/share/wordlist/rockyou.txt as our wordlist.
As we can see hashcat is able to identify all passwords.
This is part-1 we will see more examples in next part-2.
Hashcat — A password recovery tool
You can create rules by creating a file called custom.rule and using these commands: https://hashcat.net/wiki/doku.php?id=rule_based_attack.
After that use the flag -r to be able to use the rule created:
hashcat -m 0 -a 0 -D2 example0.hash example.dict -r rules/custom.rule S # By clicking s you can check at any time the status Generate a mutate password list based on a custom.rule:
hashcat --force password.list -r custom.rule --stdout > mutated_password.list Mask attacks
These are the possible masks that you can use:
?l = abcdefghijklmnopqrstuvwxyz ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ ?d = 0123456789 ?h = 0123456789abcdef ?H = 0123456789ABCDEF ?s = «space»!"#$%&'()*+,-./:;?@[\]^_`<|>~ ?a = ?l?u?d?s ?c = Capitalize the first letter and lowercase others ?sXY = Replace all instances of X with Y. ?b = 0x00 - 0xff ?$! Add the exclamation character at the end. Hashcat will apply the rules of custom.rule for each word in password.list and store the mutated version in our mut_password.list accordingly.
Example of a mask attack:
hashcat -m 0 -a 3 example0.hash ?l?l?l?l?L?l?l?la # first 8 letter will be lowercase and the ninth one will be from the all-character pool Hashcat and John come with pre-built rule lists that we can use for our password generating and cracking purposes. One of the most used rules is best64.rule
Cracking Password of Microsoft Word file
cd /root/Desktop/ /usr/share/john/office2john.py MS_Word_Document.docx > hash cat hash MS_Word_Document.docx:$office$*2013*100000*256*16*ff2563844faca58a12fc42c5036f9cf8*ffaf52db903dbcb6ac2db4bab6d343ab*c237403ec97e5f68b7be3324a8633c9ff95e0bb44b1efcf798c70271a54336a2 Remove the first part. Hash would be $office$*2013*100000*256*16*ff2563844faca58a12fc42c5036f9cf8*ffaf52db903dbcb6ac2db4bab6d343ab*c237403ec97e5f68b7be3324a8633c9ff95e0bb44b1efcf798c70271a54336a2 hashcat -a 0 -m 9600 --status hash /root/Desktop/wordlists/1000000-password-seclists.txt --force # -a 0: dictionary mode # -m 9600: Set method to MS Office 2013 # --status : Enable automatic update of the status screen Resources
Modules cheatsheet
mode 7300: IPMI
For cracking hashes from IPMI service: In the event of an HP iLO using a factory default password, we can use this Hashcat mask attack command
hashcat -m 7300 ipmi.txt -a 3 ?1?1?1?1?1?1?1?1 -1 ?d?u Mode 1000
Mode 1800: unshadow file
hashcat -m 1800 -a 0 /tmp/unshadowed.hashes rockyou.txt -o /tmp/unshadowed.cracked hashcat
advanced password recovery
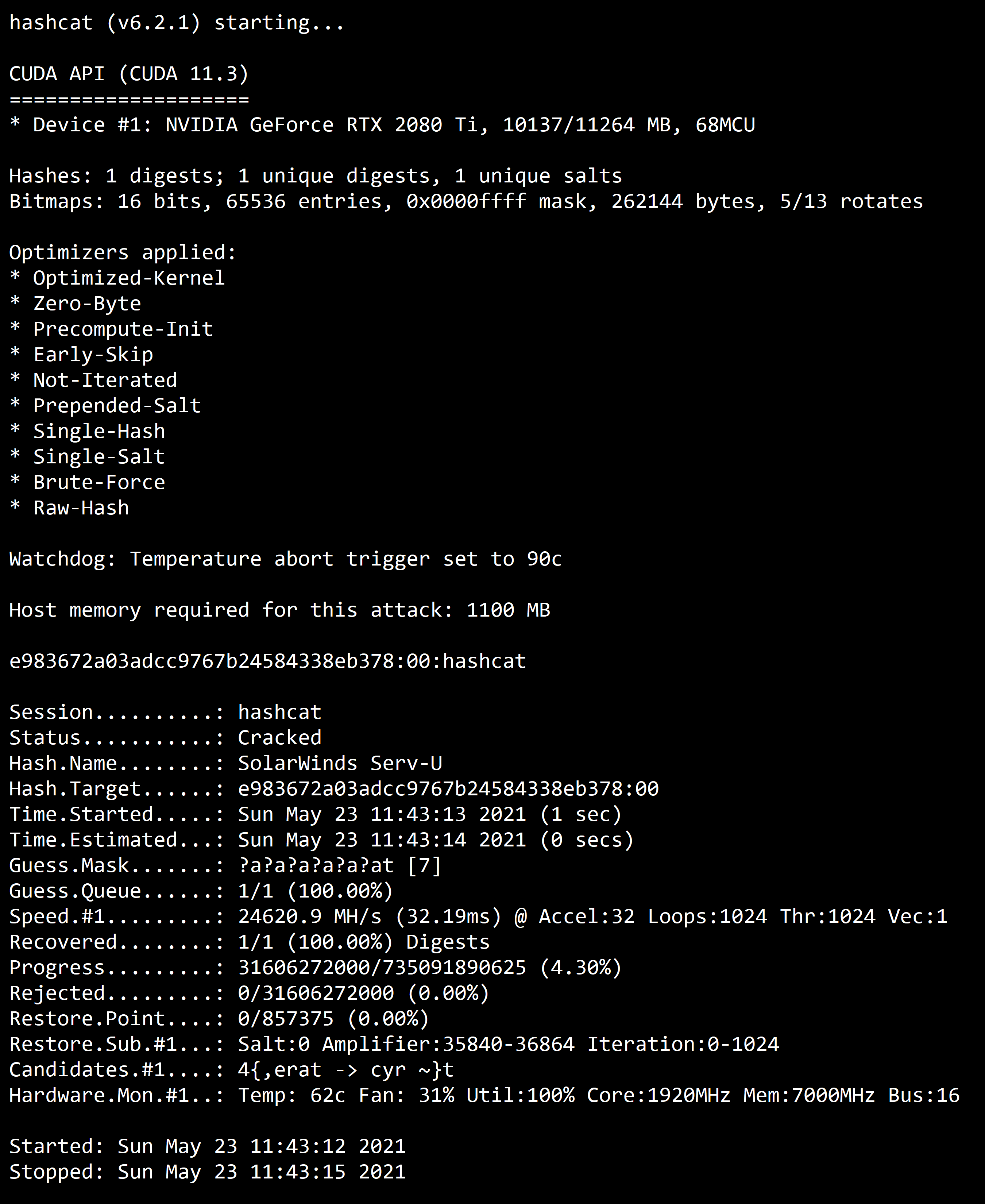
A detailed description of all commandline parameters is available by using --help. Next to that, the 7zip-package contains extensive documentation. Look for examples.txt. If you encounter a Bug, report it in the Forums where Fixes and Beta versions are announced as well.
If you still think you need help by a real human come to #hashcat on Libera.Chat IRC.
Download older version(s)
This is a list of older hashcat versions, it’s not always bad to grab the latest version.
| Name | Version | Date | Download | Signature |
|---|---|---|---|---|
| hashcat binaries | v6.2.5 | 2021.11.21 | Download | PGP |
| hashcat sources | v6.2.5 | 2021.11.21 | Download | PGP |
| hashcat binaries | v6.2.4 | 2021.08.29 | Download | PGP |
| hashcat sources | v6.2.4 | 2021.08.29 | Download | PGP |
| hashcat binaries | v6.2.3 | 2021.07.16 | Download | PGP |
| hashcat sources | v6.2.3 | 2021.07.16 | Download | PGP |
| hashcat binaries | v6.2.2 | 2021.06.13 | Download | PGP |
| hashcat sources | v6.2.2 | 2021.06.13 | Download | PGP |
| hashcat binaries | v6.2.1 | 2021.05.15 | Download | PGP |
| hashcat sources | v6.2.1 | 2021.05.15 | Download | PGP |
| hashcat binaries | v6.2.0 | 2021.05.14 | Download | PGP |
| hashcat sources | v6.2.0 | 2021.05.14 | Download | PGP |
| hashcat binaries | v6.1.1 | 2020.07.29 | Download | PGP |
| hashcat sources | v6.1.1 | 2020.07.29 | Download | PGP |
| hashcat binaries | v6.1.0 | 2020.07.28 | Download | PGP |
| hashcat sources | v6.1.0 | 2020.07.28 | Download | PGP |
| hashcat binaries | v6.0.0 | 2020.06.16 | Download | PGP |
| hashcat sources | v6.0.0 | 2020.06.16 | Download | PGP |
| hashcat binaries | v5.1.0 | 2018.12.02 | Download | PGP |
| hashcat sources | v5.1.0 | 2018.12.02 | Download | PGP |
| hashcat binaries | v5.0.0 | 2018.10.28 | Download | PGP |
| hashcat sources | v5.0.0 | 2018.10.28 | Download | PGP |
| hashcat binaries | v4.2.1 | 2018.08.07 | Download | PGP |
| hashcat sources | v4.2.1 | 2018.08.07 | Download | PGP |
| hashcat binaries | v4.2.0 | 2018.08.02 | Download | PGP |
| hashcat sources | v4.2.0 | 2018.08.02 | Download | PGP |
| hashcat binaries | v4.1.0 | 2018.02.21 | Download | PGP |
| hashcat sources | v4.1.0 | 2018.02.21 | Download | PGP |
| hashcat binaries | v4.0.1 | 2017.11.07 | Download | PGP |
| hashcat sources | v4.0.1 | 2017.11.07 | Download | PGP |
| hashcat binaries | v4.0.0 | 2017.10.27 | Download | PGP |
| hashcat sources | v4.0.0 | 2017.10.27 | Download | PGP |
| hashcat binaries | v3.6.0 | 2017.06.09 | Download | PGP |
| hashcat sources | v3.6.0 | 2017.06.09 | Download | PGP |
| hashcat binaries | v3.5.0 | 2017.04.05 | Download | PGP |
| hashcat sources | v3.5.0 | 2017.04.05 | Download | PGP |
| hashcat binaries | v3.40 | 2017.03.03 | Download | PGP |
| hashcat sources | v3.40 | 2017.03.03 | Download | PGP |
| hashcat binaries | v3.30 | 2017.01.06 | Download | PGP |
| hashcat sources | v3.30 | 2017.01.06 | Download | PGP |
| hashcat binaries | v3.20 | 2016.12.02 | Download | PGP |
| hashcat sources | v3.20 | 2016.12.02 | Download | PGP |
| hashcat binaries | v3.10 | 2016.08.19 | Download | PGP |
| hashcat sources | v3.10 | 2016.08.19 | Download | PGP |
| hashcat binaries | v3.00 | 2016.06.29 | Download | PGP |
| hashcat sources | v3.00 | 2016.06.29 | Download | PGP |
При подготовке материала использовались источники:
https://upadhyayraj.medium.com/hashcat-for-beginners-part-1-a8763030ebb4
https://amandaguglieri.github.io/hackinglife/hashcat/
https://hashcat.net/